Computer scientists at New York University and Michigan State University have trained an artificial neural network to create fake digital fingerprints that can bypass locks on cell phones. The fakes are called “DeepMasterPrints”, and they present a significant security flaw for any device relying on this type of biometric data authentication. After exploiting the weaknesses inherent in the ergonomic needs of cellular devices, DeepMasterPrints were able to imitate over 70% of the fingerprints in a testing database.
An artificial neural network is a type of artificial intelligence comprising computer algorithms modeled after the human brain’s ability to recognize patterns. The DeepMasterPrints system was trained to analyze sets of fingerprint images and generate a new image based on the features that occurred most frequently. This “skeleton key” could then be used to exploit the way cell phones authenticate user fingerprints.
In cell phones, the necessarily small size of fingerprint readers creates a weakness in the way they verify a print. In general, phone sensors only capture a partial image of a print when a user is attempting to unlock the device, and that piece is then compared to the phone’s authorized print image database. Since a partial print means there are fewer characteristics to distinguish it than a full print, a DeepMasterPrint needs to match fewer features to imitate a fingerprint. It’s worth noting that the concept of exploiting this flaw is not unique to this particular study; however, generating unique images rather than using actual or synthesized images is a new development.
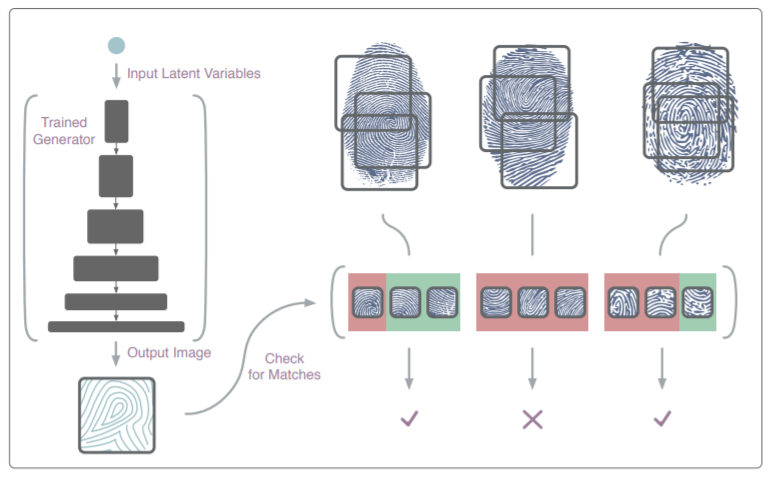
The team involved in the study resulting in the DeepMasterPrint creation initiated it as part of the ongoing assessment of vulnerabilities in fingerprint recognition systems. Finding exploitable flaws and fixing them is a constant battle in all digital systems with a security component. With this reality in mind, the scientists determined that merely exposing the flaws of fingerprint systems would not provide an effective solution; a working example of how attacks could be executed provides more specific data for researchers to design around and protect against. Creating the DeepMasterPrint system was meant to address this need.
The results revealed by the DeepMasterPrint system are concerning for anyone relying on fingerprint authentication on their smartphones. Scientists compared the generated fake prints against templates generated by VeriFinger 9.0 SDK, Bozorth3, and Innovatrics IDKit 5.3 SKD, all of which are software systems used in fingerprint authentication systems worldwide. At a low false match rate, i.e., strict match requirements for authentication, the fake print generated by DeepMasterPrint could imitate 23% of the fingerprints in the test database. At a slightly higher false match rate that was still within standard phone authentication limits, the fake print imitated 77% of the test fingerprints.
The scientists in this study did not create physical fingerprints to try and unlock actual phones, leaving that work to be done in the near future. However, even though the successful DeepMasterPrints have yet to be tested in true applications rather than a virtual environment, the data gathered confirmed the initial security concerns which inspired the experiment. Fingerprints are being used as identity verification in a growing number of applications beyond cell phone security, i.e., unlocking entryways, payment authentication, etc. The DeepMasterPrint system is another tool to help researchers guard their security as biometric authentication continues to expand.