

Firmware
Tesla extends ‘bug bounty’ to energy products, increases payout by 50%
In its continued pursuit of making the most secure internet-connected vehicles on the road, Tesla is upping the ante of its “bug bounty” program, which encourages security researchers to actively locate and report vulnerabilities on the company’s hardware and online services. As part of the program’s most recent update, Tesla has raised the maximum payout to $15,000 for vehicle or product-related vulnerabilities, while actively extending the initiative to the company’s energy products.
Just like the previous iteration of its “bug bounty” program, whose maximum payout was listed at $10,000, Tesla assured hackers that vehicles used for security research would not have their warranties voided, provided that the hacking is conducted within parameters allowed by the company. Tesla further noted that if vehicles used by participants in their good-faith security research end up being compromised, the company will take steps to update or “reflash” the hacked electric cars.
“If, through your good-faith security research, you (a pre-approved, good-faith security researcher) cause a software issue that requires your research-registered vehicle to be updated or “reflashed,” as an act of goodwill, Tesla shall make reasonable efforts to update or “reflash” Tesla software on the research-registered vehicle by over-the-air update, offering assistance at a service center to restore the vehicle’s software using our standard service tools, or other actions we deem appropriate,” Tesla noted.
Tesla’s bug bounty program started back in 2015, though the company initially invited hackers to find vulnerabilities on its website only. During that time, no vehicles were open for hacking, and the rewards offered for security researchers were far more modest at $25 to $1,000. Tesla eventually increased the scope of its bug bounty program to its vehicles, where it was eventually followed by other carmakers. Chrysler, for one, invited security researchers to hack into its Uconnect infotainment system apps and Eco-Drive driving efficiency apps in 2016.
As long as your work complies with our bug bounty policy, Tesla will not void your warranty if you hack our software https://t.co/HhibE1UpRC https://t.co/NIISSrrViD
— Tesla (@Tesla) September 5, 2018
Tesla raised the bar of its bug bounty program last September, allowing owners to actively hack into their own cars without the danger of voiding their vehicles’ warranties. The electric car maker further noted then that it would not be bringing copyright infringement claims to those working within its initiative’s rules. Bugcrowd CTO Casey Ellis, who works for the company that administers Tesla’s bounties, tweeted in support of Tesla’s initiative, stating that the move “rings a very loud bell for the legitimacy of good-faith security research.”
In a way, Tesla’s strategy towards its bug bounty program reflects the company’s Silicon Valley roots, considering that other tech giants such as Google also have active programs rewarding security researchers for finding vulnerabilities in their products. Amidst an internet landscape that is getting more and more concerned about internet security, Tesla’s security initiatives all but ensure that the company’s vehicles, while being consistently connected to the web, are as secure as possible.
Tesla’s mastery of hardware and software is among the reasons why the company is proving to be a real disruptor in the auto market. Just like Apple, Tesla adopts an in-house approach to both its software and hardware, creating a unified experience that is quite unlike anything in the market today. With the upcoming release of the first features of its Full Self-Driving suite, the rollout of Hardware 3, and the deployment of larger neural networks, Tesla’s vehicles are bound to get even more connected than before.
The electric car maker does not really announce the bugs that are being reported to the company, though several new features of Tesla’s electric cars are borne from the efforts of security researchers, including the “PIN to Drive” feature.
Newly discovered vulnerabilities must be reported within 168 hours and zero minutes, or 7 days from when the vulnerability was first discovered, to qualify for a reward. More details about Tesla’s updated bug bounty program can be accessed here.
Firmware
Tesla mobile app shows signs of upcoming FSD subscriptions

It appears that Tesla may be preparing to roll out some subscription-based services soon. Based on the observations of a Wales-based Model 3 owner who performed some reverse-engineering on the Tesla mobile app, it seems that the electric car maker has added a new “Subscribe” option beside the “Buy” option within the “Upgrades” tab, at least behind the scenes.
A screenshot of the new option was posted in the r/TeslaMotors subreddit, and while the Tesla owner in question, u/Callump01, admitted that the screenshot looks like something that could be easily fabricated, he did submit proof of his reverse-engineering to the community’s moderators. The moderators of the r/TeslaMotors subreddit confirmed the legitimacy of the Model 3 owner’s work, further suggesting that subscription options may indeed be coming to Tesla owners soon.
Did some reverse engineering on the app and Tesla looks to be preparing for subscriptions? from r/teslamotors
Tesla’s Full Self-Driving suite has been heavily speculated to be offered as a subscription option, similar to the company’s Premium Connectivity feature. And back in April, noted Tesla hacker @greentheonly stated that the company’s vehicles already had the source codes for a pay-as-you-go subscription model. The Tesla hacker suggested then that Tesla would likely release such a feature by the end of the year — something that Elon Musk also suggested in the first-quarter earnings call. “I think we will offer Full Self-Driving as a subscription service, but it will be probably towards the end of this year,” Musk stated.
While the signs for an upcoming FSD subscription option seem to be getting more and more prominent as the year approaches its final quarter, the details for such a feature are still quite slim. Pricing for FSD subscriptions, for example, have not been teased by Elon Musk yet, though he has stated on Twitter that purchasing the suite upfront would be more worth it in the long term. References to the feature in the vehicles’ source code, and now in the Tesla mobile app, also listed no references to pricing.
The idea of FSD subscriptions could prove quite popular among electric car owners, especially since it would allow budget-conscious customers to make the most out of the company’s driver-assist and self-driving systems without committing to the features’ full price. The current price of the Full Self-Driving suite is no joke, after all, being listed at $8,000 on top of a vehicle’s cost. By offering subscriptions to features like Navigate on Autopilot with automatic lane changes, owners could gain access to advanced functions only as they are needed.
Elon Musk, for his part, has explained that ultimately, he still believes that purchasing the Full Self-Driving suite outright provides the most value to customers, as it is an investment that would pay off in the future. “I should say, it will still make sense to buy FSD as an option as in our view, buying FSD is an investment in the future. And we are confident that it is an investment that will pay off to the consumer – to the benefit of the consumer.” Musk said.
Firmware
Tesla rolls out speed limit sign recognition and green traffic light alert in new update
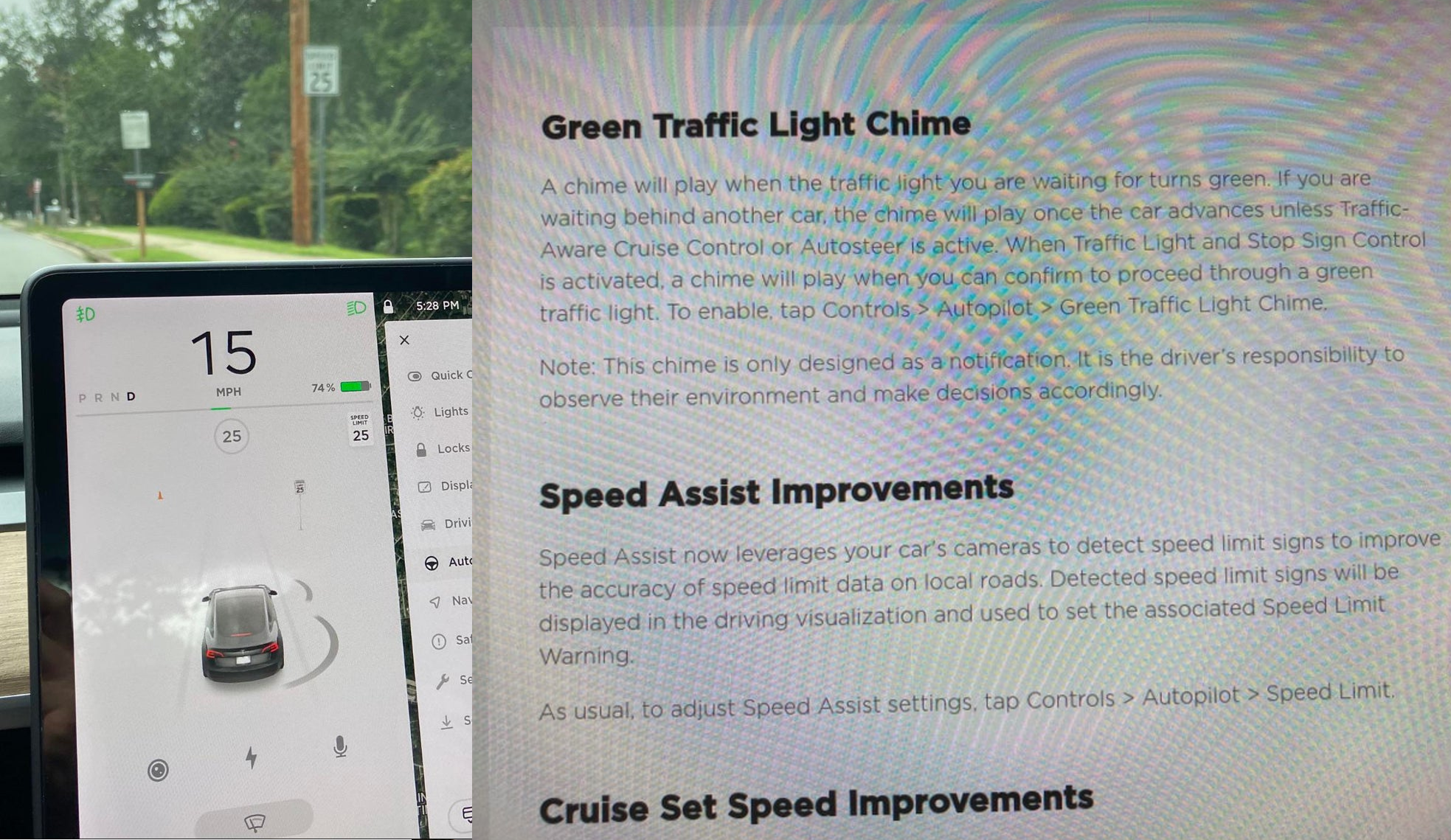
Tesla has started rolling out update 2020.36 this weekend, introducing a couple of notable new features for its vehicles. While there are only a few handful of vehicles that have reportedly received the update so far, 2020.36 makes it evident that the electric car maker has made some strides in its efforts to refine its driver-assist systems for inner-city driving.
Tesla is currently hard at work developing key features for its Full Self-Driving suite, which should allow vehicles to navigate through inner-city streets without driver input. Tesla’s FSD suite is still a work in progress, though the company has released the initial iterations of key features such Traffic Light and Stop Sign Control, which was introduced last April. Similar to the first release of Navigate on Autopilot, however, the capabilities of Traffic Light and Stop Sign Control were pretty basic during their initial rollout.
2020.36 Showing Speed Limit Signs in Visualization from r/teslamotors
With the release of update 2020.36, Tesla has rolled out some improvements that should allow its vehicles to handle traffic lights better. What’s more, the update also includes a particularly useful feature that enables better recognition of speed limit signs, which should make Autopilot’s speed adjustments better during use. Following are the Release Notes for these two new features.
Green Traffic Light Chime
“A chime will play when the traffic light you are waiting for turns green. If you are waiting behind another car, the chime will play once the car advances unless Traffic-Aware Cruise Control or Autosteer is active. When Traffic Light and Stop Sign Control is activated, a chime will play when you can confirm to proceed through a green traffic light. To enable, tap Controls > Autopilot > Green Traffic Light Chime.
“Note: This chime is only designed as a notification. It is the driver’s responsibility to observe their environment and make decisions accordingly.”
Speed Assist Improvements
“Speed Assist now leverages your car’s cameras to detect speed limit signs to improve the accuracy of speed limit data on local roads. Detected speed limit signs will be displayed in the driving visualization and used to set the associated Speed Limit Warning.
“As usual, to adjust Speed Assist settings, tap Controls > Autopilot > Speed Limit.”
Footage of the new green light chime in action via @NASA8500 on Twitter ✈️ from r/teslamotors
Amidst the rollout of 2020.36’s new features, speculations were abounding among Tesla community members that this update may include the first pieces of the company’s highly-anticipated Autopilot rewrite. Inasmuch as the idea is exciting, however, Tesla CEO Elon Musk has stated that this was not the case. While responding to a Tesla owner who asked if the Autopilot rewrite is in “shadow mode” in 2020.36, Musk responded “Not yet.”
Firmware
Tesla rolls out Sirius XM free three-month subscription

Tesla has rolled out a free three-month trial subscription to Sirius XM, in what appears to be the company’s latest push into making its vehicles’ entertainment systems more feature-rich. The new Sirius XM offer will likely be appreciated by owners of the company’s vehicles, especially considering that the service is among the most popular satellite radios in the country today.
Tesla announced its new offer in an email sent on Monday. An image that accompanied the communication also teased Tesla’s updated and optimized Sirius XM UI for its vehicles. Following is the email’s text.
“Beginning now, enjoy a free, All Access three-month trial subscription to Sirius XM, plus a completely new look and improved functionality. Our latest over-the-air software update includes significant improvements to overall Sirius XM navigation, organization, and search features, including access to more than 150 satellite channels.
“To access simply tap the Sirius XM app from the ‘Music’ section of your in-car center touchscreen—or enjoy your subscription online, on your phone, or at home on connected devices. If you can’t hear SiriusXM channels in your car, select the Sirius XM ‘Subscription’ tab for instruction on how to refresh your audio.”
Tesla has actually been working on Sirius XM improvements for some time now. Back in June, for example, Tesla rolled out its 2020.24.6.4 update, and it included some optimizations to its Model S and Model X’s Sirius XM interface. As noted by noted Tesla owner and hacker @greentheonly, the source code of this update revealed that the Sirius XM optimizations were also intended to be released to other areas such as Canada.
Interestingly enough, Sirius XM is a popular feature that has been exclusive to the Model S and X. Tesla’s most popular vehicle to date, the Model 3, is yet to receive the feature. One could only hope that Sirius XM integration to the Model 3 may eventually be included in the future. Such an update would most definitely be appreciated by the EV community, especially since some Model 3 owners have resorted to using their smartphones or third-party solutions to gain access to the satellite radio service.
The fact that Tesla seems to be pushing Sirius XM rather assertively to its customers seems to suggest that the company may be poised to roll out more entertainment-based apps in the coming months. Apps such as Sirius XM, Spotify, Netflix, and YouTube, may seem quite minor when compared to key functions like Autopilot, after all, but they do help round out the ownership experience of Tesla owners. In a way, Sirius XM does make sense for Tesla’s next-generation of vehicles, especially the Cybertruck and the Semi, both of which would likely be driven in areas that lack LTE connectivity.
-

 Elon Musk3 days ago
Elon Musk3 days agoTesla investors will be shocked by Jim Cramer’s latest assessment
-

 News1 week ago
News1 week agoTesla Robotaxi’s biggest challenge seems to be this one thing
-

 News2 weeks ago
News2 weeks agoTexas lawmakers urge Tesla to delay Austin robotaxi launch to September
-
 Elon Musk2 weeks ago
Elon Musk2 weeks agoFirst Look at Tesla’s Robotaxi App: features, design, and more
-

 Elon Musk2 weeks ago
Elon Musk2 weeks agoxAI’s Grok 3 partners with Oracle Cloud for corporate AI innovation
-

 News2 weeks ago
News2 weeks agoSpaceX and Elon Musk share insights on Starship Ship 36’s RUD
-

 News2 weeks ago
News2 weeks agoWatch Tesla’s first driverless public Robotaxi rides in Texas
-

 News2 weeks ago
News2 weeks agoTesla has started rolling out initial round of Robotaxi invites














